
Last Week in Kubernetes Development
Stay up-to-date on Kubernetes development in 15 minutes a week.
Week Ending August 26, 2018
Community Meeting Summary
This week’s community meeting began with a demo of KeyCloak, an open-source Identity Access Management (IAM) tool for Kubernetes. Stian Thorgensen demonstrated using it for external authentication with Ingress; it can be used for token-based application auth, or for logging into Kubernetes itself.
SIG-Openstack’s Chris Hoge talked about their recent work: they created the external Cloud Provider plugin, added the Manilla Storage Provisioner for shared storage, and created a keystone authenticator, and wrote a lot of docs on how to use the Cloud Provider API. They decided to delay deprecation of the in-tree Openstack provider until 1.13 to give folks time to migrate. Other future work includes certifying Magnum, supporting autoscaling, and transitioning from a SIG to being a WG of SIG-Cloud-Provider.
Saad Ali of SIG-Storage presented on their work for 1.12. They will be moving topology-aware volume scheduling from cloud-provider-specific code to a generic API on top of CSI, meaning some of the provider-specific code is going away. Snapshot & restore support will be available in alpha, and CSI is going GA.
Matt Farina shared SIG-Apps’ current work, including: finishing the SIG-Apps charter, adding recommended labels for Helm apps, and have started work on an Application specification and API for CRD-based apps. For the Workloads API, development continues on Lifecycle Hooks, Pod disruption budget, and giving Jobs deterministic pod names. Work continues on the Kompose project. The Helm project has been moved out of SIG-Apps and into its own CNCF project and Github namespace, except for Charts, which stays where it is in order to take advantage of Prow automation.
Aaron Crickenberger offered an update on automation progress: all repos are in sigs.yaml and have the canonical list of Labels, and only one repo doesn’t have OWNERs. They are currently getting repos to use the same merge automation, and discussing /retest and /lifecycle stale. Deploying Tide for merges is ready, but on-hold until after 1.12 release.
Steering Committee elections have started, and nominations are open until Sept. 14th. You can now register for the Seattle Contributor Summit through your Kubecon registration, and the same goes for the Shanghai New Contributor Workshop and Doc Sprints.
Release Schedule
Next Deadline: Code Slush, August 28th
That’s right, Code Slush starts this week. It’s time to clean up and finalize your PRs, and if that feature you’re working on isn’t stable yet, punt it to 1.13. Code Freeze starts a week later. CI Signal is not looking good, so we need everyone focused on fixing bugs.
In order to simplify contributions, Release Lead Tim Pepper has proposed to remove several required labels, most notably status/approved-for-milestone, from PRs and issues during Code Freeze. This would reduce the number of required labels to four (sig/, kind/, milestone, and priority/critical-urgent) from seven for 1.11. This proposal should pass by lazy consensus Aug. 27th.
The 1.10.7 update was released last week, including multiple fixes for the Metadata Agent.
KEP of the Week
Tim AllClair shared KEP 0014, which proposes RuntimeClass, instead of having choice of runtime performed in a completely opaque way in the Kubelet. The idea is to support alternate runtimes like Katacontainers and GVisor, allowing users to chose desired runtime via Podspec. Short-term goals are a minimal implementation; future goals include Pod Overhead and abstract RuntimeClasses, like “sandbox.” Some steps have been merged, see below.
Featured PRs
#58679: Support annotations for admission webhook
A new AuditAnnotations field in the admission webhook response struct allows
setting arbitrary key/value pairs which get written to the audit log. This can
be used to record data related to the webhook call for future debugging or
analysis.
#66971: #50102 Task 2: Add UntilWithSync
A follow up to #66906 last
week, this adds a new UntilWithSync method to avoid some common bugs when
writing watches. This new kind of watch will survive timeouts, reconnects, and
other conventional client-side errors. The downside is that the guarantees are
not quite as strong as a basic Until call, mostly with respect to event ordering
and duplication. If you want to write a long-lived watch, consider if UntilWithSync
can do the job.
#67518: Add RuntimeHandler to the CRI RunPodSandboxRequest and #67737: Runtimeclass pod API
A double header, two parts of kubernetes/features#585 got merged
this week. The first adds a handler configuration layer to the low-level CRI
interface, allowing some configuration of the underlying container runtime from
higher levels of the system. This is paired with adding a RuntimeClassName
field to the PodSpec API. It’s not yet hooked up to anything, but eventually
will let pods select specific container runtimes or configurations of a single
runtime.
#67675: Pass files to golint one at a time
Rather than passing large ranges of files into golint, it will now pass files
in one at a time. This should provide better output, as golint exits on the
first fatal error in any file.
#66257 Kubelet creates and manages node leases
Per KEP 009, the SIG-Node folks have been working on ways to improve and reduce node status polling. The alpha-gated NodeLease system is the new mechanism; default leases are 40 seconds.
Other Merges
- PodReadinessGate is now on by default
- Kubeadm has HA upgrade, can now support more than one control plane, and has a new
--rootfsoption - Azure changes: Dynamic volume limits, cross-resource-group nodes, change default disk type
- API paging for CRDs and API aggregation now works
- Cloud Providers now report hostname addreses, including OpenStack, AWS
- cli-runtime now has its own staging repo
- Headless services without ports are fixed
- Containers no longer start if they require unavailable device plugins
- Switch from using
sync.Mutextosync.mapfor a net 3% scheduler performance improvement.
Deprecated
- The in-tree OpenStack cloud provider will be deprecated in version 1.13. Migrate to the external plugin soon.
- Kubeadm is now blocking usage of HighAvailability, SelfHosting, CertsInSecrets feature-gates in Kubeadm clusters.
- The Daemonset Rescheduler is going away
Version Updates
Graph of the Week
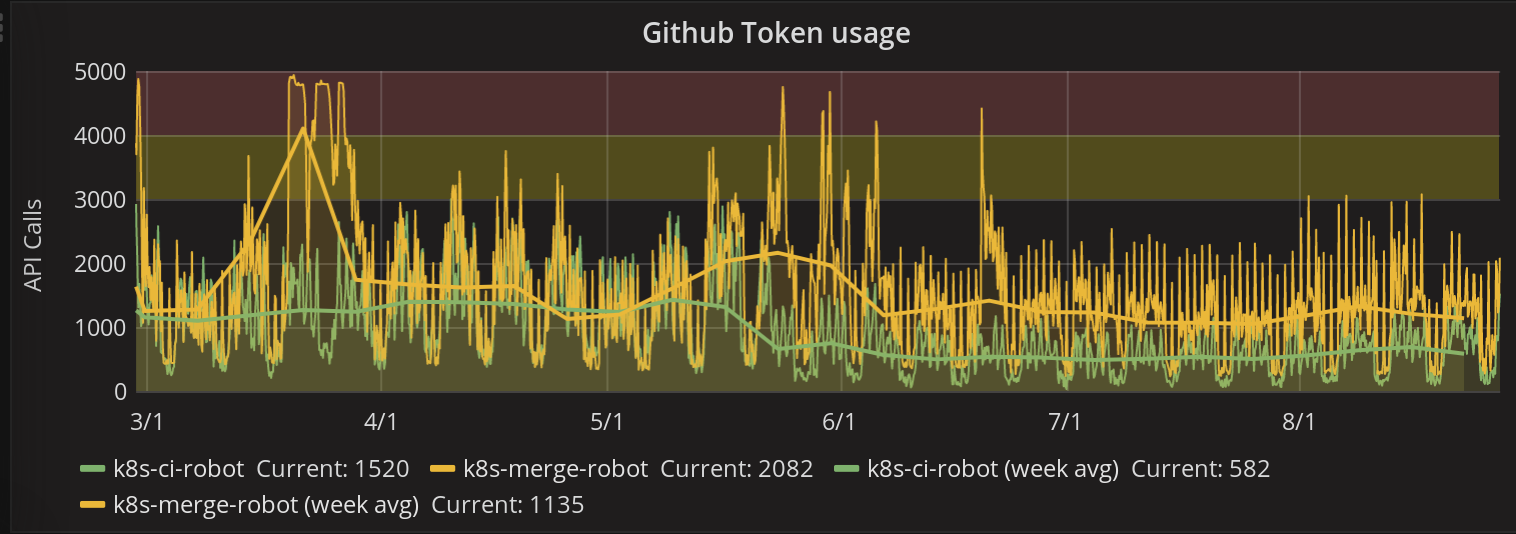
This week’s graph shows the success the Test-Infra automation has had in managing our GitHub API Token usage. While moving from mungers to the polling-based Prow helped for a bit, what really made the difference was Cole Wagner’s ghproxy tool, a cache for GitHub tokens. You can see in this graph the difference between 1.10 end-of-Freeze and 1.11 end-of-freeze; before the proxy, we were at max token usage for two days, as opposed to just minutes at a time. More token usage graphs here and here.
Last Week In Kubernetes Development (LWKD) is a product of multiple contributors participating in Kubernetes SIG Contributor Experience. All original content is licensed Creative Commons Share-Alike, although linked content and images may be differently licensed. LWKD does collect some information on readers, see our privacy notice for details.
You may contribute to LWKD by submitting pull requests or issues on the LWKD github repo.